Introduction
Discover how our latest project revolutionizes Threat Intelligence, offering tech businesses powerful protection against evolving cyber threats.
Imagine a fast-developing tech company nestled in the heart of Copenhagen—let’s refer to them as Company C. As they expand their digital footprint, they find themselves increasingly in the crosshairs of cyber threats. Recognizing early warning signs, such as suspicious network activities and unusual data access patterns, they understand the imperative need for effective risk management to protect their valuable data, maintain their hard-earned reputation, and ensure uninterrupted operations. Determined to stay ahead of potential disasters, they sought a comprehensive, proactive solution.
Challenge
Company C required a holistic approach to monitor a spectrum of digital threats spanning illicit darknet forums, social media, exposed critical services, fraudulent domain registrations, and leaked credentials databases. They needed a solution not just for today but one that could evolve with the digital landscape and the unique threats they face. Facing these challenges head-on, Company C turned to SAGA by Munit.io—a cutting-edge platform engineered to offer flexibility, scalability, and accuracy in navigating the complex terrain of digital risk protection.
Solution: Munit.io‘s SAGA®
• Extensive Digital Threat Surveillance: SAGA® empowers Company C with the capability to monitor emerging threats across diverse digital arenas, including the dark web, places where data is leaked, and private chat services. This makes sure they miss nothing in keeping safe online.
• Tailored Threat Intelligence Alerts: Customization is key. SAGA® delivers personalized alerts that match Company C’s specific risk profile, helping them act fast to stop problems.
• Flexible Integration Options: Recognizing that one size does not fit all, SAGA® offers various deployment models. This flexibility allows seamless API integration with Company C’s existing infrastructure, catering to their operational needs without compromise.
Implementation Plan
Starting to improve online safety with Munit.io‘s SAGA® involves carefully planned steps to make sure Company C’s online world is secure against new and changing threats.
• Initial Threat Assessment: We start by checking out Company C’s online presence to spot weaknesses and risks. This first step helps us know where to focus our protection efforts.
• Setting Up Ongoing Monitoring: With the insights garnered from the initial assessment, we set up a monitoring strategy as unique as the digital signature of the company. This involves pinpointing critical digital assets, sensitive data repositories, and potential entry points for cyber adversaries.
• Continuous Monitoring: SAGA® is always on guard, looking for signs of data theft, leaks, or other cyber dangers across the internet. It pays attention to hidden online places and public ones, catching any hint of trouble.
• Alert Customization: Precision in alerts is crucial. It’s important that alerts are clear and useful. We make sure Company C gets information about real dangers to their business, nothing unnecessary.
• Regular Reporting and Analysis: We regularly communicate with Company C about what we find, including any threats and what to do about them. This isn’t just a list of problems; it’s a full review with advice on how to stay safe.
• Response Planning and Action: We help Company C get ready to deal with threats. This means making a plan to lessen risks and avoid future problems.
• Ongoing Training and Support: Equipping via knowledge is our final step. We offer ongoing training and support, ensuring the company’s team is not just trained with a tool but armed with knowledge.
Selecting Keywords for Precision Monitoring:
Picking the right keywords to watch is crucial. We don’t just cast a wide net; we carefully choose words that are most likely to signal real threats. This includes terms specific to Company C’s industry, their products, key employees, and important projects.
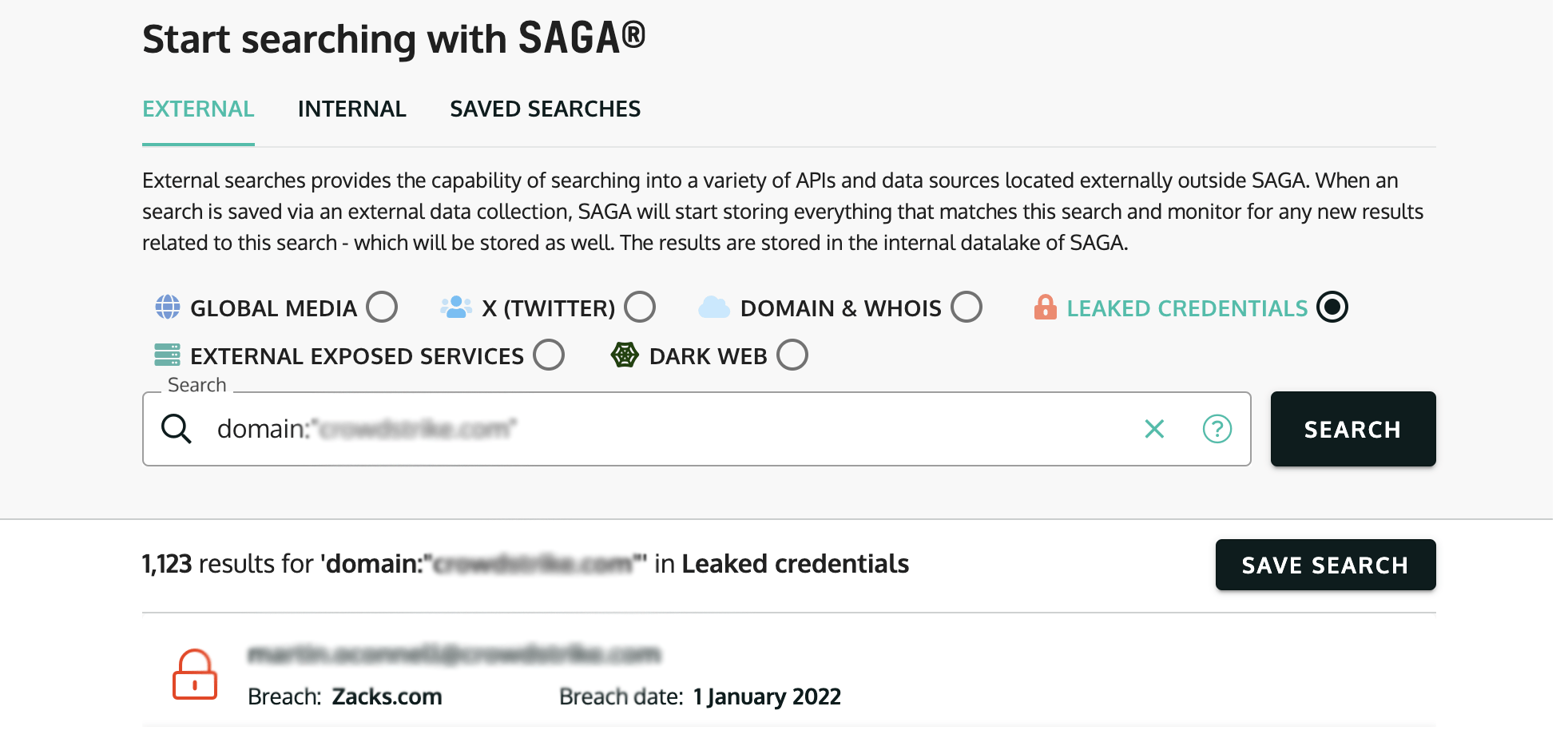
Identifying Keywords:
• Industry-Specific Terms: We start with a foundation of terms unique to the tech sector and Company C’s specific niche, ensuring we are attuned to threats targeting similar entities.
• Company Assets: Names of proprietary technologies, services, and product names form a key part of our lexicon, guarding against intellectual property theft and counterfeit risks.
• High-Value Personnel: References to high-profile employees or executives are monitored to protect against targeted attacks or information leaks.
• Sensitive Projects: Keywords related to upcoming launches or critical projects are included to preempt leaks or sabotage efforts.
Leveraging AI for Contextual Analysis
With large amounts of information, it’s tough to find what’s truly important. That’s where SAGA®’s smart AI comes in. It looks at every alert, figures out what’s a danger, follows trends in cyber threats, and suggests how to deal with problems. This helps Company C understand and act on threats more effectively.
AI-Driven Insights:
• Threat Contextualization: The AI system categorizes each finding, whether it’s a potential data breach, a discussion around a vulnerability, or an imminent threat of attack. This context helps Company C understand not just that a threat exists, but the nature and urgency of it.
• Trend Analysis: Over time, the AI identifies trends in the cyber threat landscape, offering insights into evolving tactics or emerging threats specifically targeting the tech industry or Company C’s operational geography.
• Mitigation Recommendations: Beyond identification, the AI suggests preliminary steps for mitigation based on the nature of the detected threats, enabling Company C to respond swiftly and effectively.
Real-World Impact
For Company C, this approach transformed the deluge of digital noise into a stream of precise, actionable intelligence. For instance, when the AI identified discussions around a zero-day vulnerability in software commonly used by Company C, it not only alerted the company but also provided context about the discussions’ seriousness and potential impact. Equipped with this insight, Company C was able to patch its systems before any exploit occurred proactively.
Similarly, when the system flagged an increase in dark web chatter mentioning Company C’s flagship product by name, the AI’s contextual analysis revealed a planned DDoS attack. This early warning enabled Company C to bolster its defenses and coordinate with its ISP to mitigate the impact.
Conclusion
This case study highlights the transformative power of Munit.io‘s SAGA® in equipping small and medium-sized tech enterprises with a challenging protection mechanism against the intricate and ever-evolving cyber threat landscape. By integrating custom keyword selection with cutting-edge AI-driven contextual analysis, SAGA® exceeds traditional digital threat monitoring. It offers a proactive, intelligent solution that not only identifies but contextualizes and prioritizes cyber threats, enabling businesses to act fast and effectively. This strategic approach ensures that companies like Company C are not just respondents to cyber threats but are empowered to anticipate, understand, and neutralize potential risks before they occur. In an era where digital presence is equivalent to survival, SAGA® stands as a lighthouse of resilience, safeguarding the digital boundaries of today’s tech innovators.
