5 common types of phishing attacks
Do you like fishing? Cybercriminals all around the world love it, but they catch users, not fish. This process is called phishing – attacks based on social engineering tactics that range from classic email schemes to increasingly sophisticated approaches. All have the same purpose: get personal information by making users believe a message they hear or read and download an attachment or follow the link. It can be a request from a bank, a note from someone in the company, or password verification. Read about the most popular types of phishing to protect you and your company from this cyber disaster.
Email phishing
The most familiar type of phishing started in the 1990s and is still a very effective way for criminals to obtain private information by sending emails to billion of people. These emails usually ask to verify the details of your account or tell that there has been a compromise to your account and that immediate actions like clicking on a provided link or downloading the document should be taken.
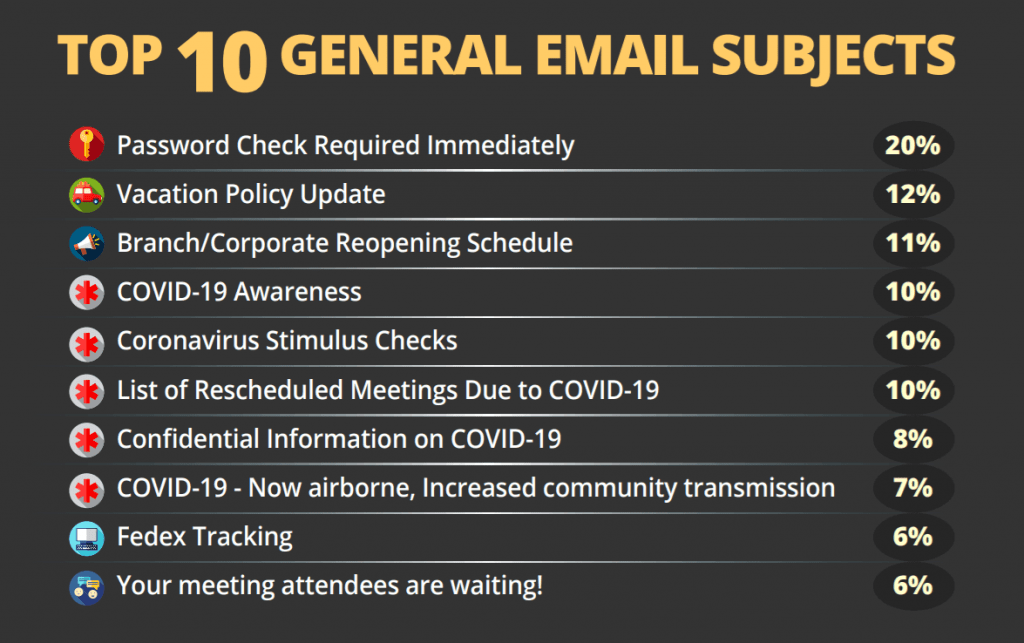
Here is the list of top-clicked phishing emails according to a Q2 2020 report from security awareness training company KnowBe4. As you can see, the COVID-19 pandemic has given criminals a big opportunity to increase the number of their victims.
The evolution of social media and services you can be subscribed to has armed hackers a powerful weapon – online impersonation. Just take a look at this screenshot and try to see the sights of scammers impersonating Netflix:
- poor English
- strange email address
- a hidden link that tries to take you to a dodgy website

There are many ways to spot phishing emails, but as a general rule always check the email and the website addresses that as you click a link or download some attachment.
Spear phishing
This type of crime is very similar to email phishing, but it uses more targeted approaches. Instead of sending out emails to thousands of recipients, criminals choose certain employees at specific companies. These emails are crafted carefully in a more personalized way: hackers use real names, addresses, job functions, or phone numbers to make you believe the sender and follow the instructions mentioned in the email.
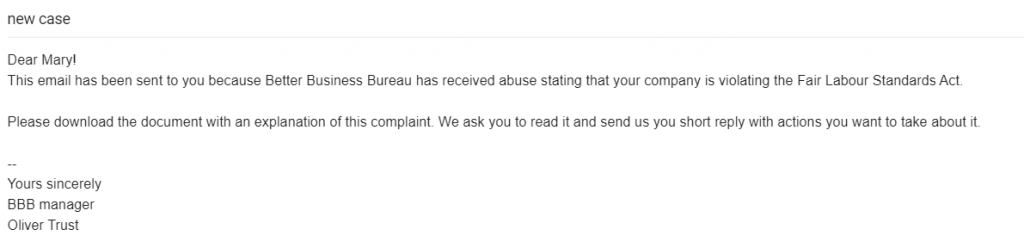
Whaling
Whale phishing is a type of phishing aimed at the really “big fish” – CEOs, CFOs, or other high-value targets. It requires social engineering to get information about the business and the person to create an ideal “hook” that would make a victim believe this email. These messages usually inform the board members about critical situations and ask them to download documents connected to mentioned business issues or visit some links and complete tax information. Sometimes attackers impersonate senior leadership members using similar email addresses. The email might ask the company employees for money transfers, personal information, or request to download and review documents. Thinking that a sender is a real person from a company, employees download the malware or share confidential information without any hesitation.
According to the 2021 Cybersecurity Census Report, 36% of IT leaders are not disclosing breaches and whaling for fear that they may lose their job, complicating efforts to enhance security.
Vishing
“Voice phishing” is a type of crime where attackers use phone calls or voice messages. Pretty often these calls and voices are disguised as messages from financial institutions or tech support that ask recipients to provide their account information, PIN, or passwords for security reasons. These scams manipulate people’s feelings working with fears of their devices or bank accounts getting hacked. The amount of vishing calls usually increases during stressful times. During COVID-19 pandemic many people receive fake calls from health organizations impersonators informing about future vaccination or new types of Corona found in the neighbourhood and the urge of providing social security numbers. The criminals play with fears and create a sense of panic and urgency, so the recipients are tricked easily.
Smishing
The type of phishing that uses manipulative text messages to steal personal and corporate information is getting more and more popular.
What makes smishing so profitable for scammers? According to the recent SMS marketing statistics:
- 9 out of 10 people open their text messages.
- Text messages have a 209% higher response rate than emails, phone calls, and Facebook messages.
The most common example is a text message containing a link that leads to malware. Being immediately installed on your smartphone after clicking the link, the malware is used to log your keystrokes, steal your identity or valuable files.
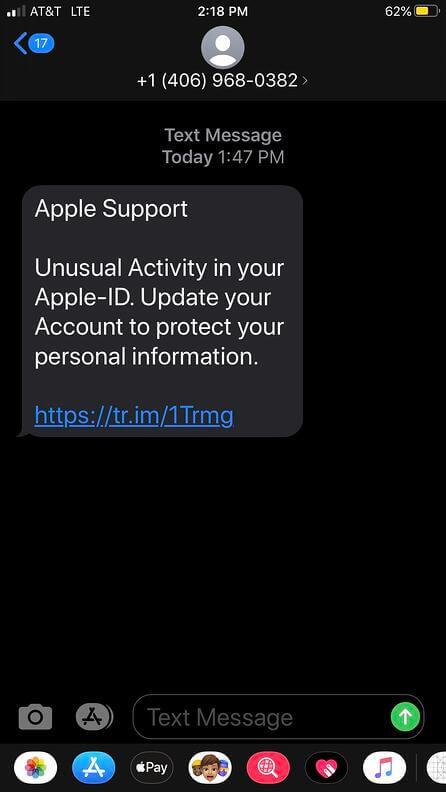
Another possible way for criminals to make you pay for nothing is to make you send a one-word response to the text. In this situation, the transaction would be triggered and lead to fraudulent charges in the future.
Cybercriminals will continue using phishing emails as long as they are producing a great deal of profit. Training yourself, your team, and relatives can help to stay secure and defend your personal information.